Information Security
Management System
By creating and maintaining an Information Security Management System you can greatly increase employee participation in maintaining a safe and secure work environment.
You company must protect corporate information and customer information.
Every employee must understand corporate concern with information security. Management's must make all personnel aware of pertinent practices, and the requirement to understand and heed them.
However, an effective Information Security Management System cannot be solely defined in terms of trust. Rather, it must be based upon the same prudent business practices that applied to earlier manual systems;
- careful definition of individual responsibilities
- separation of controls
- maintenance of audit trails
- protection of vital records
- access to information limited, based on "need-to-know"
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
An effective Information Security Management System includes
- awareness
- education
- training
- policies
- procedures
- controls
- reviews
- separation of responsibilities.
However, an Information Security Management System requires more than correct practices to be effective. They must have real and continued management backing and involvement. Management must be pro-active regarding Information Security Practices. They must let their people know it's important through example. They must take pride in their program. They must help bring about attitudinal changes in their people through; strongly administered security awareness programs; bringing about a clear understanding of the reasoning behind the Information Security Management System. They must instill real concern about Information Security; and instill dissatisfaction with anything less than great Information Security.
In addition, to be successful with the Information Security Management System, the company must also organize their team with clearly defined roles and responsibilities, with no conflicts of interest. Separation of responsibilities must be an integral part of Information Security. Training must be provided as required.
Further, management must also learn to manage "smarter". The multitude of practices required to address Information Security Management System issues, and the associated workload to do so, mandates that management be imaginative in administering the responsibilities and to maintain them on an ongoing basis.
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
Laws
Both federal and state regulations exist, which relate to control of, and authorized access to, information and computer resources. The Foreign Corrupt Practices Act of 1977 made most corporate managers and directors personally liable for assuring that "transactions are properly authorized, transactions are properly recorded, and access to assets is properly controlled". Management must provide shareholders with reasonable assurances that accurate books and records are properly maintained, and that the business is adequately controlled.
The Copyright Act of 1976 reaffirmed that computer programs and software are protected under the Federal Copyright Law. One must read and understand licensing agreements before attempting to make copies of programs or documentation. All of the United States has enacted Computer Crime Laws that establish specific penalties for unauthorized persons attempting to access a computer system, or assisting someone in gaining unauthorized access to a computer system.
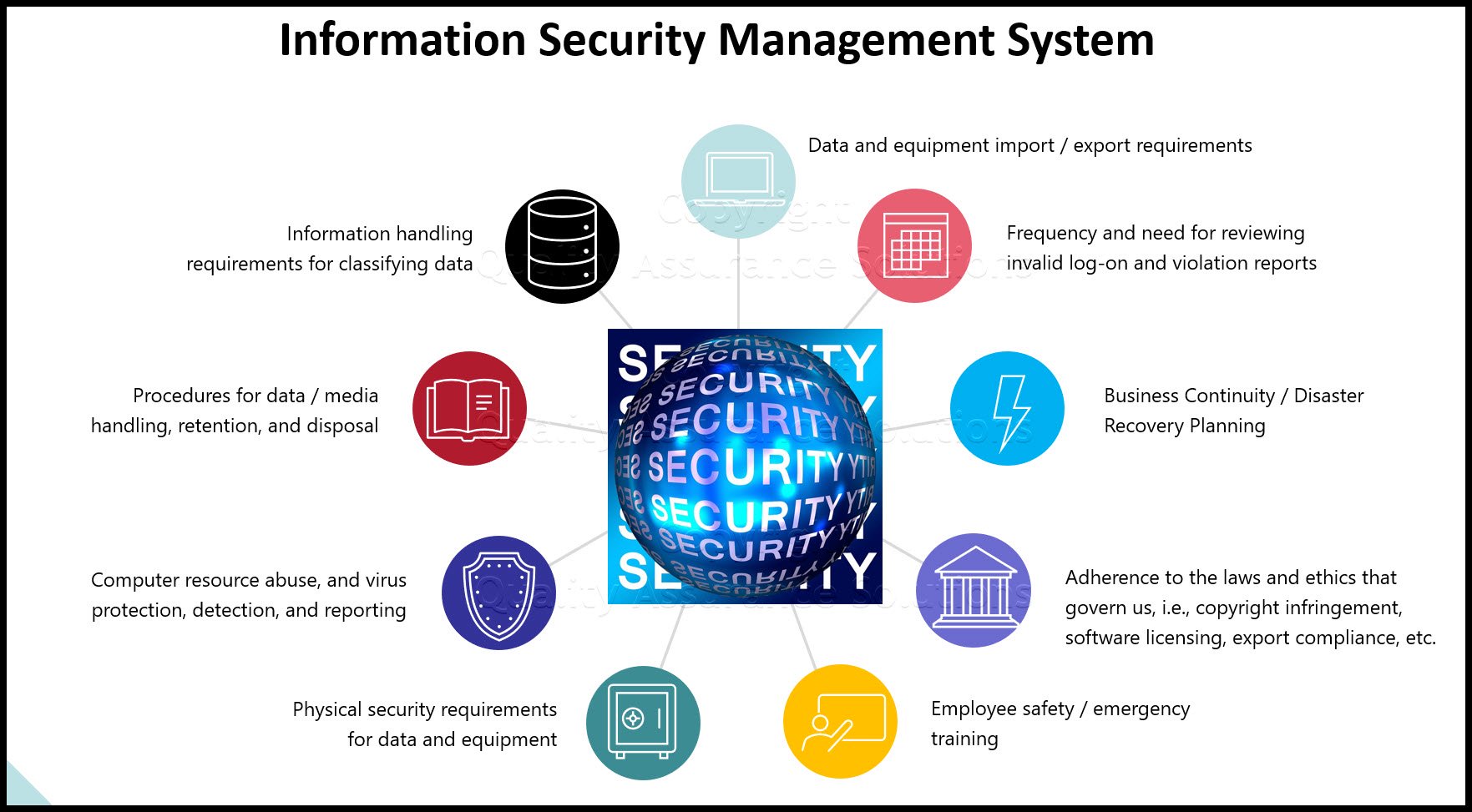
Important Contents of Information Security Management System
- Information handling requirements for classifying data
- Procedures for data / media handling, retention, and disposal
- Computer resource abuse, and virus protection, detection, and reporting
- Physical security requirements for data and equipment
- Data and equipment import / export requirements
- Frequency and need for reviewing invalid log-on and violation reports
- Business Continuity / Disaster Recovery Planning
- Adherence to the laws and ethics that govern us, i.e., copyright infringement, software licensing, export compliance, etc.
- Employee safety / emergency training (for example, evacuation routes, shelter locations, hazardous material training, fire training, blood-borne pathogen awareness)
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Every employee must understand the rationale behind the Information Security Management System in place. To facilitate that goal, an ongoing awareness program to educate employees about the practices should be established. Management should make information protection awareness a job description key element, and a part of each employee's annual evaluation, at a minimum.
The main responsibility for a successful implementation of Information Security Management System lies with people. Awareness and understanding develops information protection conscious work habits.
Your company must be concerned with adherence to Corporate Information Protection Policies, implementation of local procedures, promoting awareness, administering appropriate information access, and reviewing access violations. Make every manager responsible not only for the protection and integrity of assets under their control, but also for compliance with Corporate Information Protection Policies and Procedures. Each manager must make the necessary risk management decisions that consider the unique environment be prepared to justify their decisions during an IT audit.
Return On Investment (ROI)
If you implement a Program you will enable the great results that will follow from fewer (maybe zero) information security incidents (this is the ROI $), to fewer (maybe zero) audit comments written during an IT audit.
At a minimum you will have accomplished the following:
- Improved the morale of employees by providing them with information they need to perform their jobs effectively.
- Presented Information Security issues to the company leadership team on a consistent basis so that Information Security is identified as important and integral to the way you do business.
- Helped to enable good audit reports by providing employees with knowledge on Information Security issues.
- Strengthened the relationship with your customer by reinforcing good Information Security practices.
- Made employees aware of their responsibilities.
- Helped to enable the protection of information / assets.
- Helped to enable timely recovery in the event of a disaster.
Your ISO 9001:2015 Kit includes Templates, QA Manual, Implementation Guide and a Gap Assessment Internal Audit Tool for ISO 9001:2015
Establish Information Security Resources
You need to develop the plan to implement your security strategy - that means the allocation of human resources. To achieve greater efficiency and lessen the staffing impact, you need to implement solid hardware and software standards, streamline processes, and define metrics to establish the baseline and continually measure progress.
It is very important to allocate an appropriate percentage of employees to the information security challenge, especially in the area of technical support.
The following areas need to be staffed / represented / addressed
- A Chief Security Officer (CSO) should be appointed, or at a minimum someone should be officially designated to be the point person for Information Security... there needs to be a champion.
- Policy development.
- Ongoing employee awareness program.
- Administration, e.g., problem resolution, rights and privileges, customer service.
- Architecture, e.g., security strategy, standards, migration planning, project management.
- Compliance and reporting, e.g., metrics, monitoring, reporting.
- Technical support, e.g., virus control, firewalls, product evaluations, help desk.
- QAS Home
- Security
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |