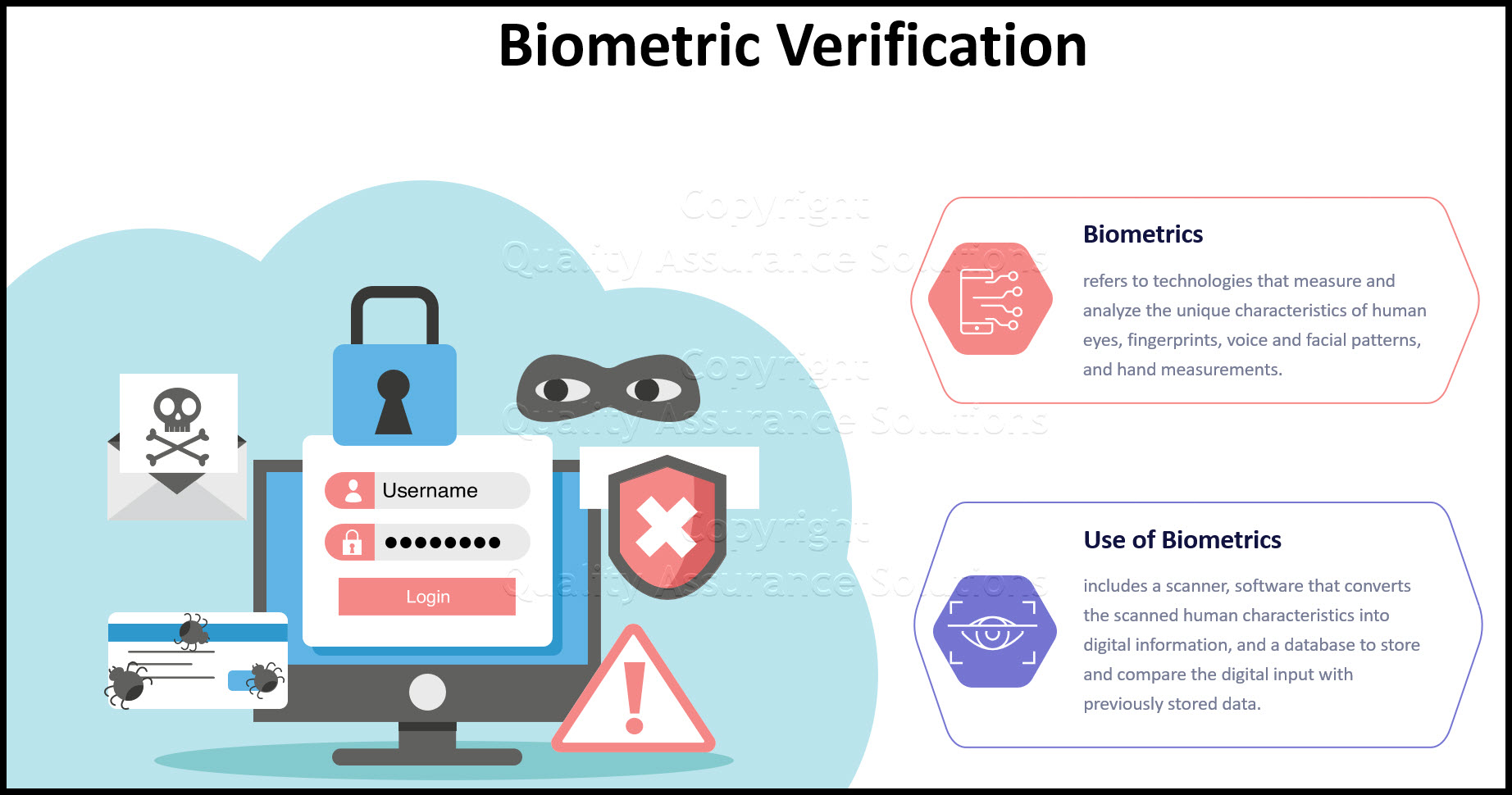
Prevent Computer
Virus Download
Keep a heightened awareness of the existence of computer viruses and the destruction that can occur when a PC is infected by one. For example, the threat of the Michelangelo computer virus download, received widespread attention. Virus concerns prompt the installation of computer virus detection tools to prevent computer virus download
A computer virus is nothing more than software code, but this code can be destructive. In order for a PC to become infected, the code needs to be transferred to the PC and then executed. This most commonly occurs by means of an infected download or infected attachment to an e-mail message, which can come from a variety of sources.
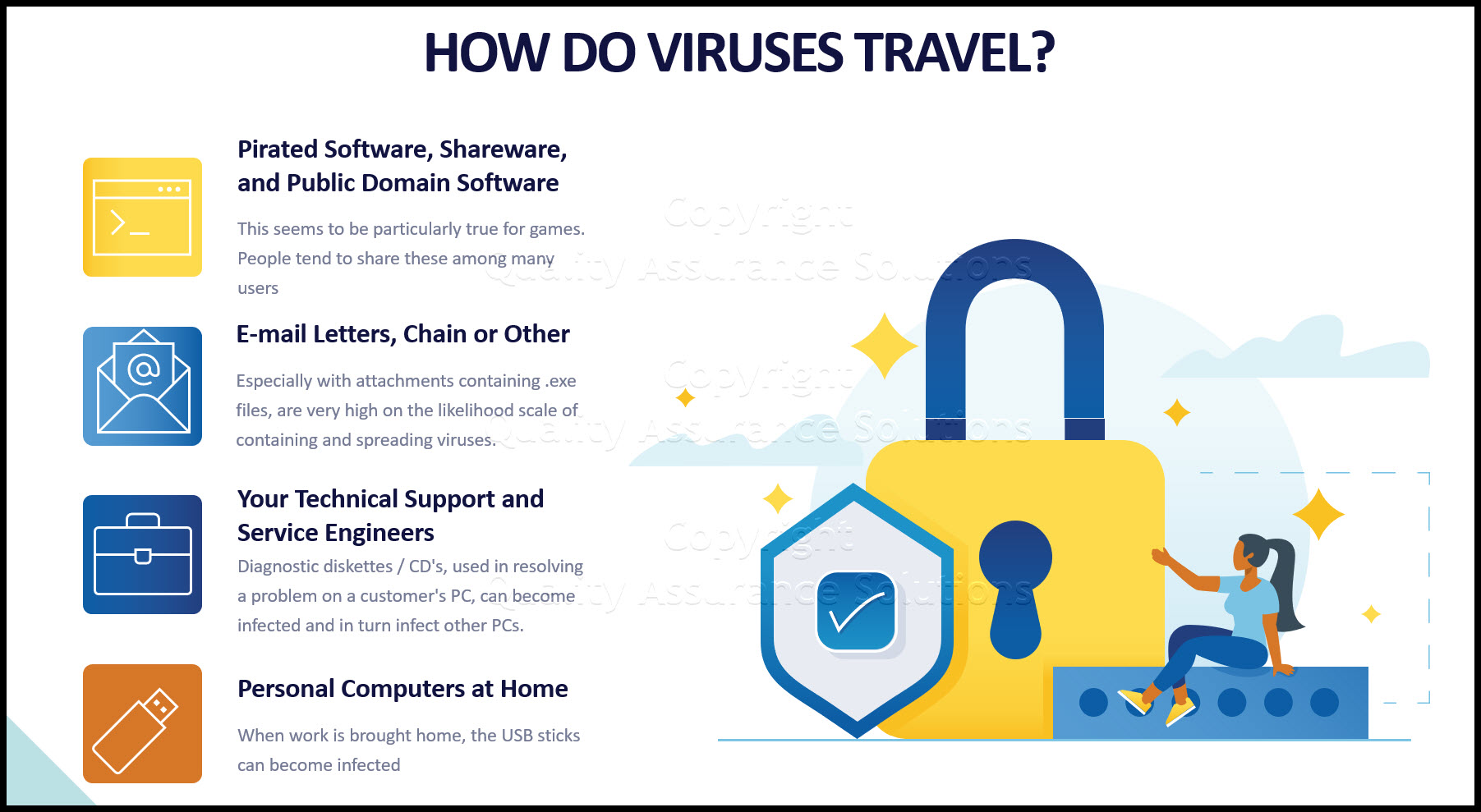
How do Viruses Travel?
Several of these are listed below...
- Pirated Software, Shareware, and Public Domain Software are common sources of viruses. This seems to be particularly true for games. People tend to share these among many users and the likelihood of a computer virus download infection increases accordingly. Try to steer clear of this type of software, or be sure to follow recommended anti-virus procedures.
- E-mail letters, chain or other, especially with attachments containing .exe files, are very high on the likelihood scale of containing and spreading viruses. Don't open these, especially if from an unknown source.
- Your Technical Support and Service Engineers can provide an effective medium for the spread of viruses. Diagnostic diskettes / CD's, used in resolving a problem on a customer's PC, can become infected and in turn infect other PCs.
- Personal computers at home can also be sources of infection. When work is brought home, the USB sticks can become infected, and then one takes back the infection to the workplace.
Purchased Software is generally virus free. Major software vendors quality assurance procedures prevent the spread of viruses through their products. Plus, if purchase software contained viruses, it would kill that company's business.
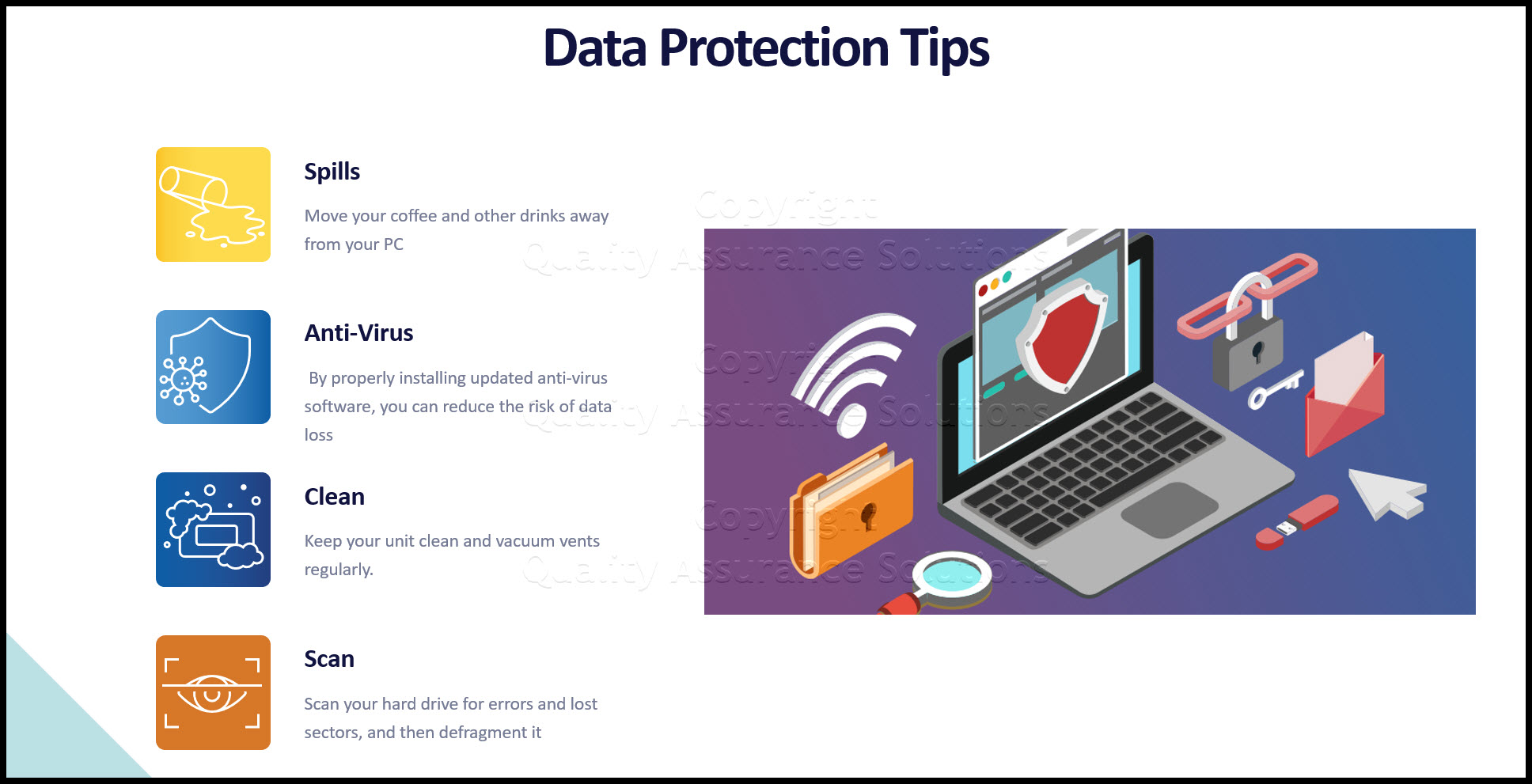
To safeguard against infection, make sure you have anti-virus software on your PC and always scan USB sticks, downloaded software, and inbound e-mail messages prior to opening / use. If you have Microsoft Windows, turn on Windows Defender.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Company Post Detection
Computer viruses cause much justifiable concern for all PC users.
What do you do when you think you have a computer virus download or someone warns you of a possible virus? if you think you may have a virus, first contact your PC help desk. Then follow the company procedures.
However, if you receive a warning such as many of us have via an e-mail message advising you to be aware of a virus, such as the "Good Times" virus, you should validate the information before sending it through your network.
The "Good Times" virus threat was a hoax. But, because people with good intentions relayed the warning throughout their networks and to friends in other companies, it had the same effect as a true virus. It caused people to take time away from their job to pass the warnings on, resulting in many hours spent not in a company's best interests. The initiators of the warning caused a disruption in business without really doing anything to your PC systems.
So, whenever you receive one of these "warnings", validate it before
you alert the world. It will save your company time. If it is a true virus, take proper action. If it is a hoax, defeat the purpose of whoever initiated it. To validate virus warnings such as this, contact your PC help desk or your favorite anti-virus vendor.

Types of Viruses
The big three are:
- Virus - A program that can attach itself to another program (the host), and then causes damage to hardware, software, and files.
- Worm - A stand-alone self-replicating program that can invade a computer, consume memory, and cause it to crash.
- Trojan Horse - A computer program that appears to be legitimate, but conceals an unexpected function which is usually damaging.
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
What to Know:
- Unless you have antivirus software installed on your computer, you won't really know if it has been infected. In many cases, a computer virus download can slow your computer's processing capability or trigger other unusual behavior, but these symptoms can also be caused by a number of unrelated reasons.
- If you notice that your computer or Internet connection seems to be running without actually using it, or if your computer settings change, these are symptoms of an infection.
- Antivirus software should be considered a vital part of any organization's defense against computer viruses. Antivirus software will not only prevent many virus infections, but will help the user detect and remove viruses.
What to Do to Prevent Computer Virus Download
Follow these steps to prevent computer virus download.
- Install antivirus software on all office machines to monitor systems for suspicious virus-like behavior.
- Keep current with the latest virus definitions by regularly visiting your antivirus software vendor's web site to download them, or by running scheduled updates to your antivirus software. Only then will your software be able to recognize the latest identified threats.
- Educate all employees on antivirus software use.
- Use scanning software in conjunction with memory-resident or integrity-checking software to provide the greatest degree of protection.
- Scan all foreign CD's and USB sticks before use.
- Regularly check your system to ensure that the antivirus software is resident and working properly.
- Keep your operating system current with the latest software patches.
- Keep your purchased software products current with the latest software patches.
- Learn about/how to set the security features on your computer.
- Install a firewall.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
What to Do if Your Computer Gets Infected
Once you have identified that you have an infection, download the latest virus definitions or updates from your antivirus software vendor's web site, and follow their directions to fix or remove the virus.
In most cases, if you download the latest virus definitions from your antivirus software vendor, that will take care of the problem. In some cases, you may also need to follow some additional steps to manually remove the infection from within your system. If you need further assistance, you can contact your antivirus software vendor for support in removing the virus.
You still need to be alert since many times a Trojan Horse is spread like a virus or with a virus, but may not show symptoms for a long time, if ever.
What to Consider:
- Make sure any computer virus download alert you receive is real and not a hoax. If you've seen, heard, or read about a virus via a reputable news media source, it is probably real. However, if you receive an e-mail from someone you know regarding a virus alert, and they ask you to pass it along, don't. This is a common ploy used by virus creators to spread the infection. Instead of just forwarding a virus alert to contacts in your address list, first confirm whether or not the virus alert is real by contacting either your local PC support team or your antivirus vendor.
- Be cautious about visiting unknown or unusual web sites. Staying on the main routes of the information highway will keep you safer.
- Don't open e-mail attachments from anyone you don't know, and be cautious of attachments from people you do know. Some viruses spread by mailing themselves to contacts in an infected computer's address book. If you have any doubts about the safety of an attachment, check with the source before opening it.
By using discretion, and keeping your antivirus software definitions current, you can guard and protect your computer system from unplanned unavailability
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
An Organizational Task Management System. Projects, Meetings, Audits & more | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
450+ Editable Slides with support links | ||
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |