Information Security Awareness Training
Please see the below components to consider when conducting Information Security Awareness Training.
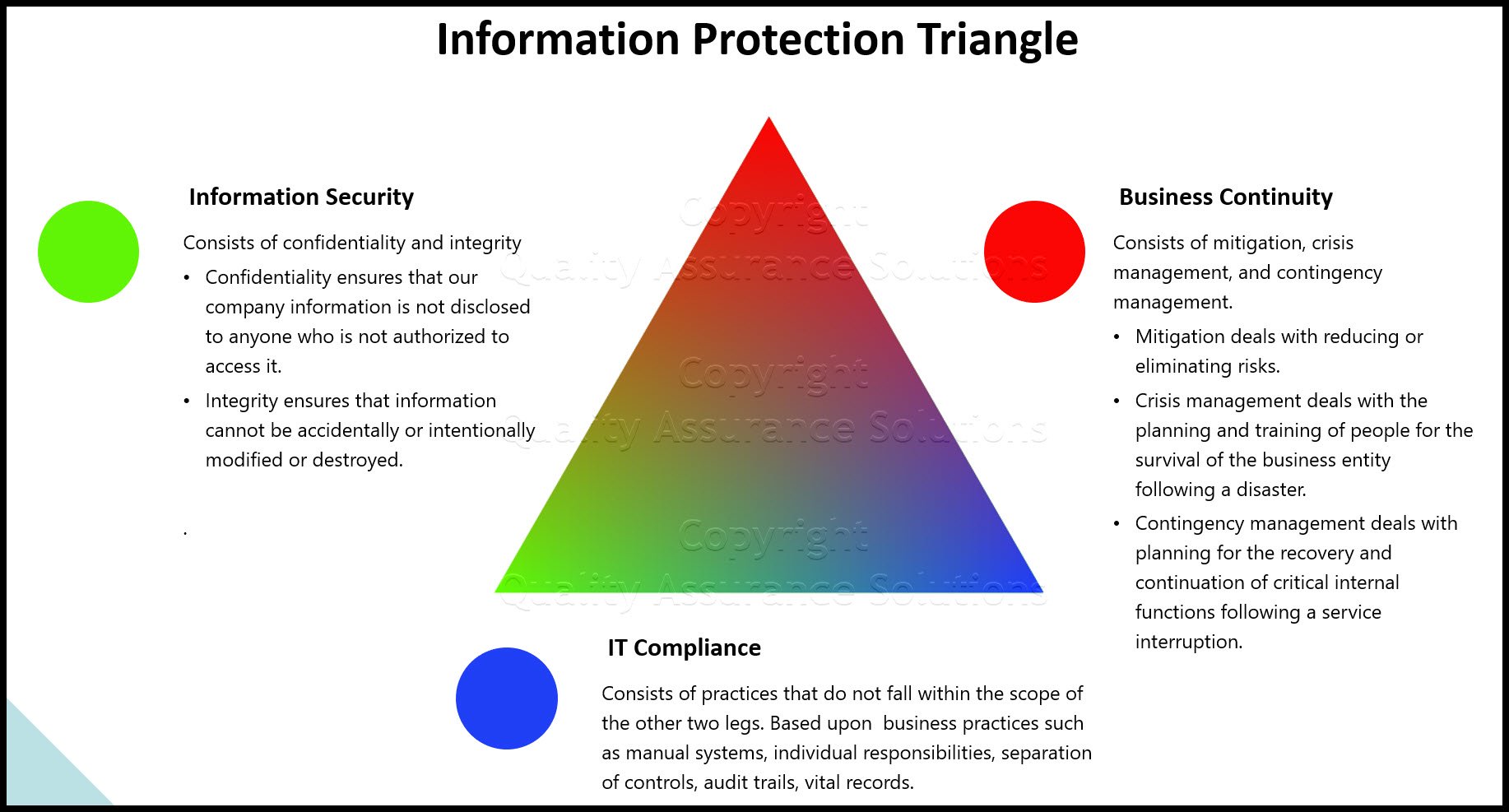
Audience Identification of Information Security Awareness Training
Consider these audiences:
- The entire company/all employees
- The entire company leadership team/all managers and supervisors
- The entire company technical team/all IT technical personnel
- The entire company administrative team/all administrative and clerical personnel
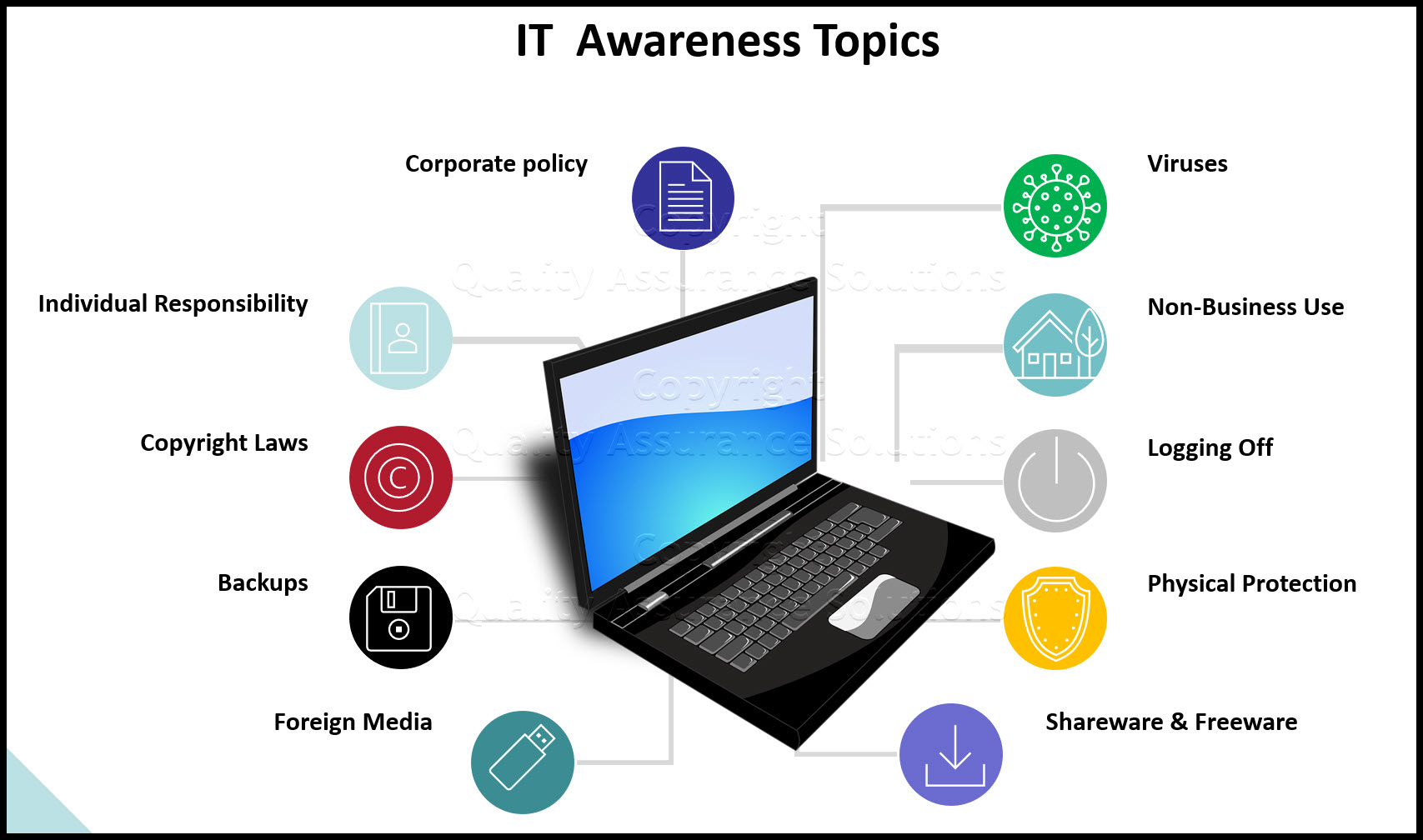
Personal Computer Wisdom
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand their individual responsibility
- to understand copyright laws
- to understand the risk with "shareware" and "freeware"
- to understand the importance of making regular backups
- to understand proper media handling
- to understand the risk with foreign media
- to understand the ramifications of viruses and how to protect against them
- to understand the policy governing non-business use
- to understand the importance of good housekeeping in the work environment
- to understand the consequences of failing to logoff
- tips regarding physical protection of laptops
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Managers’ Responsibilities
Audience: The entire company leadership team
Needs/Concerns:
- to understand corporate policy - company and customer
- to understand their individual responsibility/liability
- to understand their responsibility for the protection and integrity of assets under their control
- to understand their responsibility to promote Information Security Awareness
- obligation to see that unauthorized access violation reports are reviewed and resolved
- obligation to investigate and correct known exposures
- responsibility to ensure that information security personnel are informed of all personnel transfers and terminations
- responsibility to ensure that material is disposed of properly
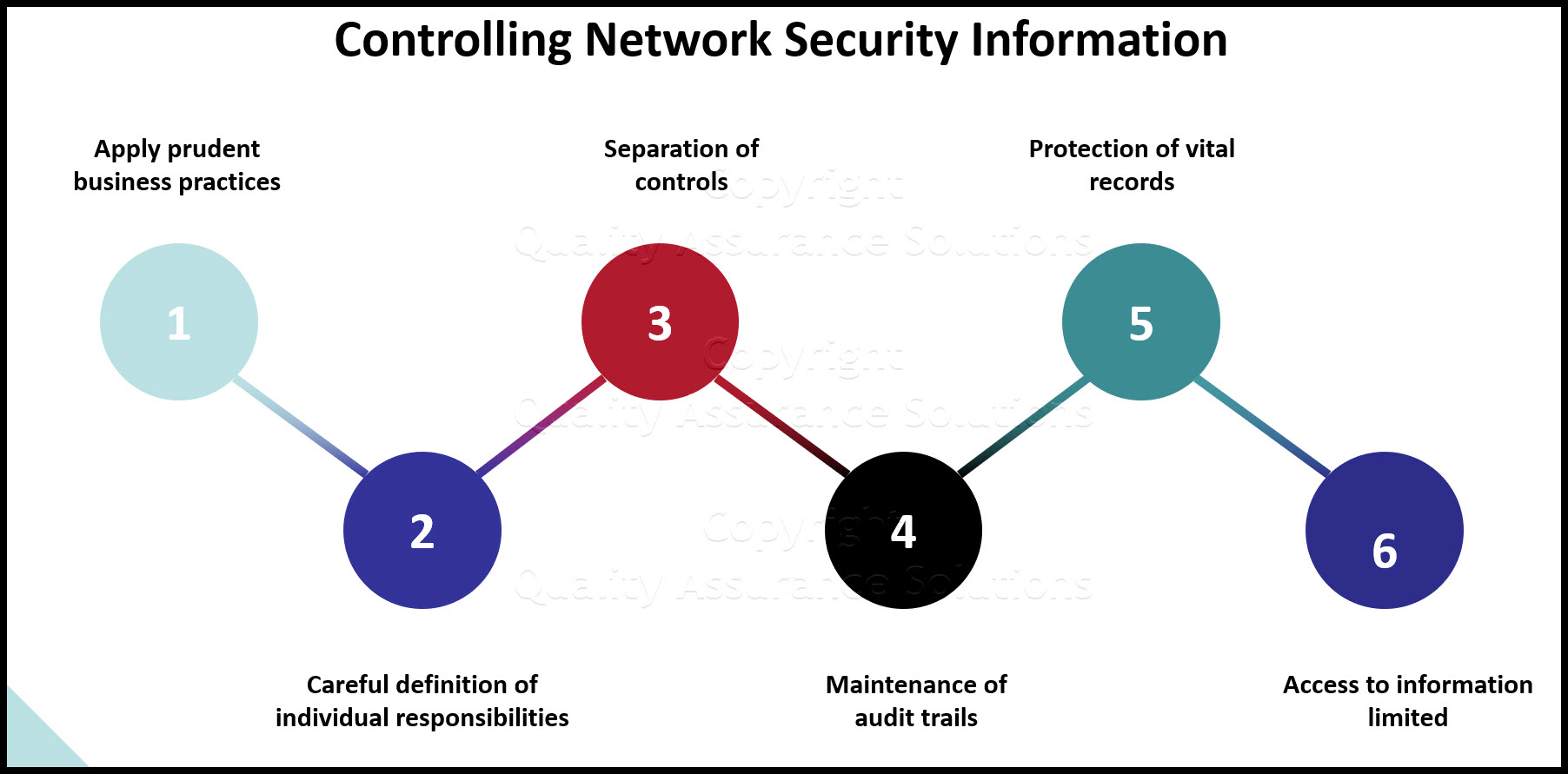
- responsibility to incorporate the segregation of duties concept where it makes good business sense
- responsibility to ensure that the overall work environment is secure, and that information is protected during all phases of testing, and that the test and production environments are kept separate
- perform periodic random reviews of employee activities and datasets to act as a deterrent against non-business use of company resources
- responsible for compliance with all corporate policy, especially Information Security and Business Continuity.
- responsibility to ensure each users access is limited to the minimum transaction and command sets necessary to accomplish assigned tasks
Employee Responsibilities
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand their individual responsibility
- to realize their ethical responsibility
- to educate them of corporate and local policies
- to make them aware of proper material disposal methods
- to make them aware of their responsibility for the protection and integrity of assets under their control
- to apprise them of good password habits
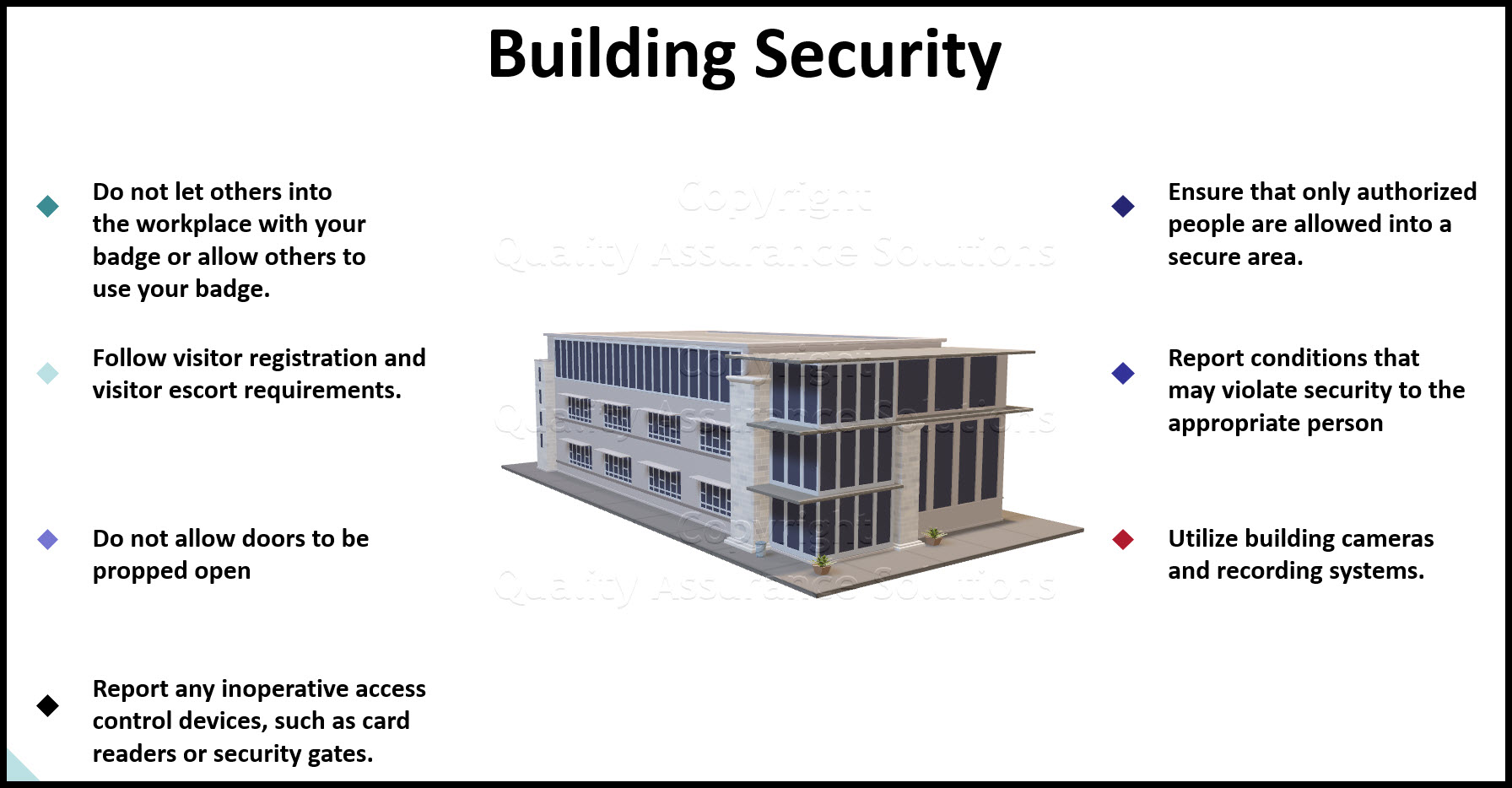
- responsibility to ensure their individual work areas are secure
- responsibility for their own individual business continuity compliance
- responsibility for physical security
- ethics as it pertains to knowledge of customer plans and information
- to understand the importance of good housekeeping in the work environment
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
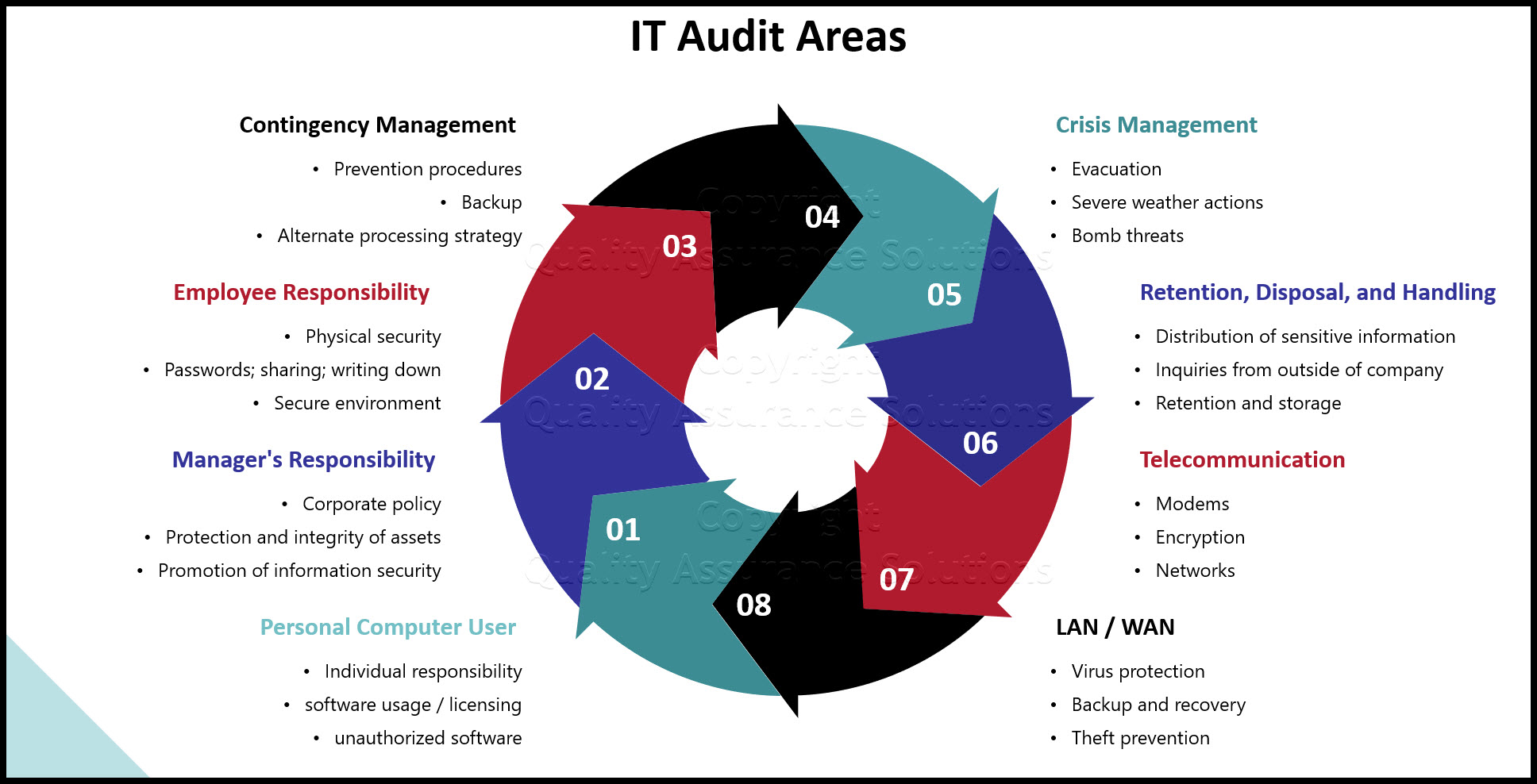
Contingency Management Issues
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand individual responsibility
- to understand customer service level requirements
- to understand proper mitigation/prevention procedures
- to understand proper backup, offsite storage, and recovery procedures
- to understand need for alternate processing strategy
- to understand need for a network recovery strategy
- to understand need to document disaster recovery plans
- to understand need to assist in development of customer reaction plan
- to understand need to do disaster recovery plan testing
- to understand benefit of continuous improvement of plans
Crisis Management Issues
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand their individual responsibility
- to understand the need for evacuation, severe weather, and bomb threat plans
- to understand what to do; where to go; who to contact
Information Retention, Disposal, and Handling Issues
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand their individual responsibility
- to understand need to identify sensitive information
- to understand need to classify sensitive information
- to provide advice concerning printing of sensitive information
- to provide advice concerning faxing of sensitive information
- to understand concerns with voice transmissions and cellular phones
- to understand proper distribution techniques regarding sensitive information
- to provide advice concerning the reproduction of sensitive information
- to provide advice on proper disposal techniques for sensitive information
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Telecommunication Issues
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand their individual responsibility
- to understand disaster recovery concerns regarding networks and PBX's
- to understand concerns with modems
- to understand need for encryption
- to apprise of latest PBX toll fraud schemes
- to understand concerns with cellular phones and voice mail
- to understand travel call card concerns
- to understand voice mail concerns and protection mechanisms
Local Area/Wide Area Network Issues
Audience: The entire company
Needs/Concerns:
- to understand corporate policy
- to understand individual responsibility
- to understand virus concerns
- to understand backup and recovery concerns
- advice on theft prevention
- to understand copyright and licensing concerns
- to understand concerns with downloading of sensitive data
- to inform of policies governing password standards
- to inform of good housekeeping practices
- to inform of local policy and procedures
- to advise of client/server risks
- to apprise of dial-up access concerns and concern with modems
Media Identification
- Newsletter
- Bulletin boards
- Desk tops
- Memorandums
- Classes
- Voice mail
Your ISO 9001:2015 Kit includes Templates, QA Manual, Implementation Guide and a Gap Assessment Internal Audit Tool for ISO 9001:2015
Communication Opportunities
Communication opportunities to reach the appropriate audience may include, but are not limited to the following:
- Leadership meetings
- Team meetings
- Planned series of desired messages using an available media type from above.
Support Definition
Materials that may be available from outside companies, or may need to be internally generated:
- Newsletter
- Brochures
- Standardized presentations
- Videos
- Posters
- Security bulletin board
- Security guidelines
- Supporting publications
- Courses
Measurement/Evaluation
To measure and evaluate the effectiveness of our awareness program, we will do the following:
- The MAIN method we will use to measure the success of our program will be to conduct mini-audits, consisting of five to ten observable items, which will be conducted before and after each main message of our program, to determine whether or not there has been any behavior change as the result of our Information Security Awareness Training program.
- Track the number of audit comments related to the issues covered by our awareness program to determine if there was a decrease.
- Track the number of viruses encountered to determine if there was a decrease.
- Conduct surveys regarding the effectiveness of our awareness program.
- Request feedback regarding our awareness program for continuous improvement.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Program Construction for Information Security Awareness Training
Program Schedule
The Master schedule/calendar of Information Security Awareness materials development, materials acquisition, and materials and message distribution.
Materials
Develop or obtain the necessary materials from an outside resource.
Communications Development
Develop communications for needs that are unique to the local organization to supplement the overall program.
Implementation
Implement the Information Security Awareness Training Program according to the schedule developed in Program Construction Section I Program Schedule. Be flexible and adjust the schedule to the immediate needs that may occur within the organization. Promote Information Security Awareness at events and opportunities as they become available.
Review/Revise Program
I. Effectiveness Measurement
Measure the effectiveness of the Information Security Awareness Training Program utilizing the activities designed in Program Design Part VI Measurement/Evaluation.
II. Feedback Review
Analyze the feedback from the measurements/evaluations and incorporate the analysis into future planning for the Information Security Awareness Training Program.
III. Revision Strategy
Review and revise materials periodically to keep them current. It is recommended this be done by building the review process into the continuing master calendar/schedule planning process.
IV. Continuous Improvement
Information Security Awareness Training is a perpetual process, it is not a "quick fix". As the Program unfolds, and feedback is received, begin performance planning for the ongoing Program. Information Security related behaviors and knowledge can always be improved.
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
An Organizational Task Management System. Projects, Meetings, Audits & more | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
450+ Editable Slides with support links | ||
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |