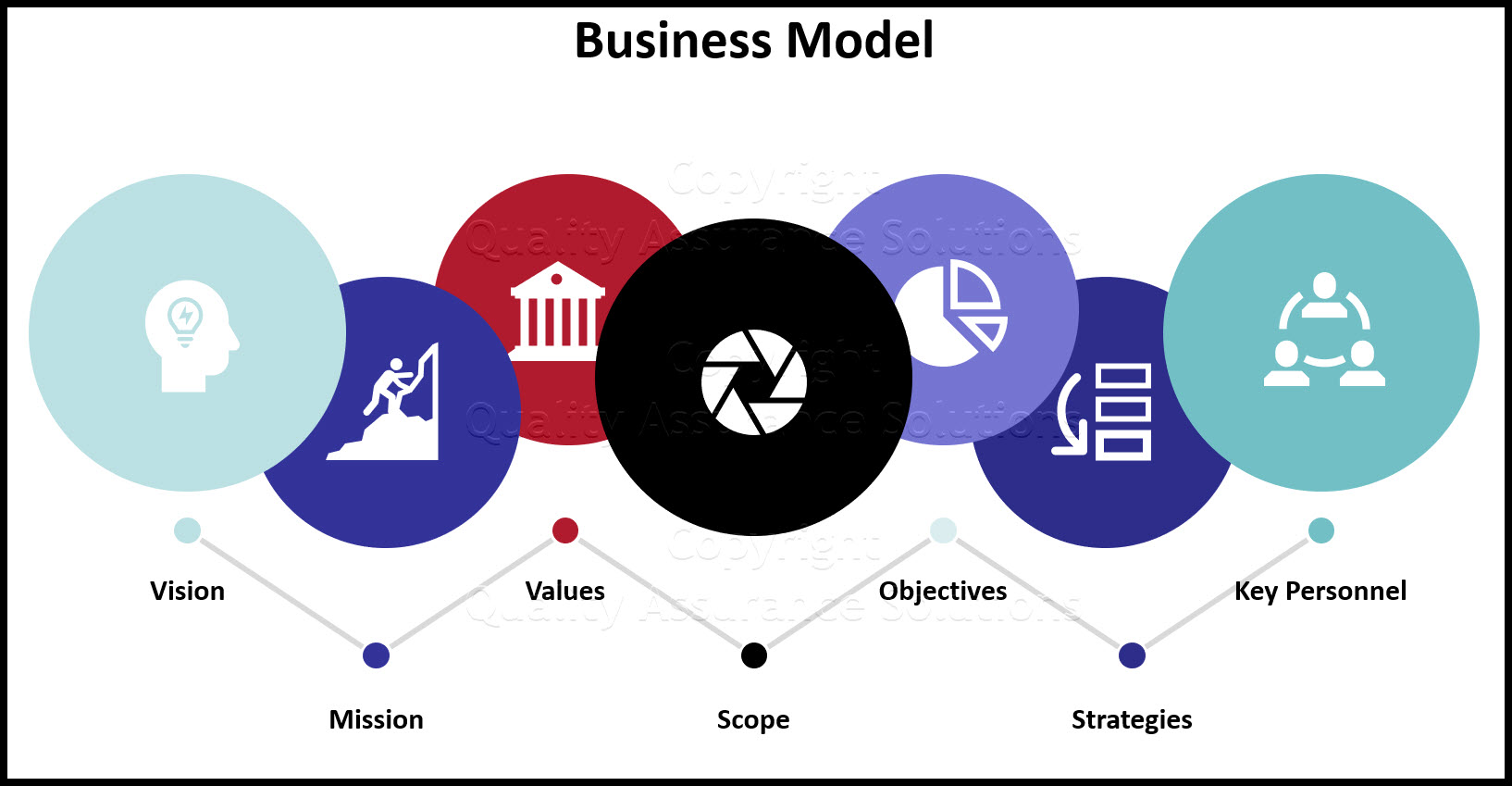
Business Model Sample
The below info provides a business model sample for a security awareness company.
Vision
Zero security incidents and zero audit comments.
Mission
Guide, direct, and
assist "Your Name Here for this business model sample" to create
and maintain an
Information Security environment,
second to none, in accordance with Corporate
Policy and sound business practice.
Values
Focus on Attitude, Communication, Continuous Improvement, Enthusiasm, Leadership, People, Reliability, Respect, and Teamwork.
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Scope
Information Security consisting of confidentiality and integrity; Business Continuity consisting of mitigation, crisis management, and contingency management; and IT Compliance consisting of sound business practices regarding adherence to the laws and ethics that govern us, in all Business Units where "Your Name Here for this business model sample" is the owner or has custodial responsibility.
Objectives for This Business Model Sample
1) Provide the Information Security Team members with the education and knowledge to be effective in their respective organizations, and disseminate that knowledge throughout their organizations.
2) Provide a consistent approach to Information Security across "Your Name Here for this business model sample".
3) Create and maintain a Corporate sense of urgency.
4) Continuously improve our effectiveness.
5) Identify and measure the quality and quantity of our efforts.
Strategies
1) Provide the Information Security Team members with the education and knowledge to be effective in their respective organizations, and disseminate that knowledge throughout their organizations.
1.1) Create the environment and the training methodologies for the Information Security Team Members to become subject matter experts in Information Security.
1.2) Provide training to the personnel with Information Security primary responsibilities.
1.3) Communicate the roles, responsibilities, and expectations of the Information Security Team to the Leadership Team to improve the effectiveness of our network thru enhanced communication and teamwork.
1.4) Encourage professional "networking".
1.5) Support technical certifications.
2) Provide a consistent approach to Information Security across "Your Name Here for this business model sample".
2.1) Provide a strategic plan to achieve and maintain Information Security excellence.
2.2) Interpret, evaluate, coordinate, and communicate Information Security requirements mandated by Corporate Policy and outside policy making bodies, i.e., Federal, State.
2.3) Provide Information Security Awareness to the entire Corporation and position ourselves for recognition by the Corporation and the Customer for providing a quality Information Security environment.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
3) Create and maintain a Corporate sense of urgency.
3.1) Serve as the aggressive communication gateway for Information Security to the Corporate Leadership Team.
3.2) Actively work as a team to effectively leverage resources.
3.3) Communicate openly with all stakeholders.
3.4) Increase awareness by providing monitoring, reviewing, status reporting, and assurance activities.
4) Continuously improve our effectiveness.
4.1) Provide a process for continuous improvement.
4.2) Identify and disseminate leading practices.
4.3) Implement cross-training to facilitate personnel backup.
4.4) Implement an organization that is "process driven".
4.5) Utilize change management methodologies.
4.6) Provide appropriate training.5) Identify and measure the quality and quantity of our efforts.
5.1) The MAIN method we will use to measure the success of our Program will be to conduct mini-audits, consisting of five to ten observable items, which will be conducted before and after each main message of our program, to determine whether or not there has been any behavior change as the result of our Awareness Program.
5.2) Track the number of audit comments related to the issues covered by our Awareness Program to determine if there was a decrease.
5.3) Track the number of viruses encountered to determine if there was a decrease.
5.4) Conduct surveys regarding the effectiveness of our Awareness Program.
5.5) Request feedback regarding our Awareness Program for continuous improvement purposes.8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Key Personnel in This Business Model Sample
Leadership
- Corporate Champion
- Divisional Managers
- Department Managers
Information Security Team
- Program Manager
- Divisional Information Security Team Members
- Department Information Security Team Members
Roles
Corporate Champion
- provide commitment and resources
- meet monthly at a minimum with Program Manager
- set direction and establish priorities
- actively address bottlenecks and deficiencies
- recognize great efforts/results
Divisional Managers
- recognize your responsibility and accountability
- provide commitment and resources
- meet monthly at a minimum with your Divisional representative
- set direction and establish priorities
- actively address bottlenecks and deficiencies
- recognize great efforts/results
Department Managers
- recognize your responsibility and accountability
- provide commitment and resources
- meet monthly at a minimum with your Department representative
- set direction and establish priorities
- actively address bottlenecks and deficiencies
- recognize great efforts/results
Your on-line Lean Six Sigma Certification. Course includes videos, reference materials, mobile app, quizzes and a certification test. Start studying today and get certified at your own pace.
Program Manager
Attributes for this Business Model Sample
- Must be able to lead
- Must be able to think.
- Must be able to communicate.
- Has an interest and/or desire to be involved in Information Security. Not a prerequisite, but a willingness to learn is essential.
- Committed to Information Security.
- Ability to keep the awareness level or "sense of urgency" within the Corporation at a high-level.
- Has an understanding of the Corporation’s business and customers. Must be able to represent the Corporation in all decisions regarding process requirements and implementation/execution.
- The ability to communicate effectively with all levels of the Corporation. Must be able to describe requirements and solicit assistance from all levels of the Corporation. This may require some selling techniques.
- Some technical knowledge and/or experience in application development and/or maintenance. This can help the person to effectively communicate concerns, and direct activities within the Corporation.
- Ability to set direction to promote consistency and quality across the Corporation.
- Ability to delegate tasks to team members when appropriate or required.
- Ability to plan. Much of the work will revolve around the development of various plans. The person should be able to develop plans that the Divisions can meet, and exert the necessary influence to see that they do.
- Ability to effectively plan and execute team meetings and projects.
Program Manager Responsibilities
- Act as the focal point and have overall Corporate responsibility for Information Security.
- Promote an active partnership with the customer, if appropriate, in addressing Information Security responsibilities and activities.
- Accesses the Corporate Champion directly, and provides regular updates on all pertinent issues, including monthly status of items being tracked.
- Provides updates at the Corporate Champion's peer meetings of pertinent information.
- Coordinate those activities deemed by the Information Security Program as "must do" activities.
- Act as liaison to Corporate and/or external Audit Staffs.
- Facilitate meetings of the Information Security Program Team in such a manner that team members have a single interpretation of requirements.
- Review Policy, Procedures, and Issues related to Information Security as to their impact on the Corporation.
- Establish a pro-active plan pertaining to audit objectives, prepare vs react.
- Coordinate the implementation of required practices and procedures.
- Obtain/demand active involvement of the Divisional Information Security Team members.
- Escalate/solve problems and conflicts.
- Recommend organizational changes to achieve Corporate objectives.
- Recommend appropriate training across the Corporation related to Information Security.
- Promote and monitor adherence to Corporate Policy.
- Promote Information Security as part of the day-to-day business within the Corporation.
- Monitor planning and status across the Corporation.
Comprehensive ISO 9001:2015 Audit Checklist for Internal, Gap and Certification Audits.
Divisional Security Team Members
The attributes and responsibilities of a Divisional Security Team Member would be the same as the Program Managers’ except that their Champion would be the Program Manager, and their audience would be their respective Division and Departmental Security Team.
Departmental Security Team Members
The attributes and responsibilities of a Departmental Security Team Member would be the same as their respective Divisional Security Team Member except that their Champion would be the Divisional Security Team Member, and their audience would be their respective Department personnel.
- QAS Home
- The Basics
- Business Model Sample
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |